¶ Basic info
There are three types of user on a Linux system
- superuser - typically root. Has full control over everything on the system. UID is 0
- system user - these are used by processes providing services. These services are usually known as daemons. These accounts will typically not be privileged users and cannot log in interactively. That is to say that an ordinary user cannot log in as a system user.
- regular user - standard user account for users to log in and use the system. Typically these are not privileged.
¶ Useful commands
Some basic information can be found out about users using a few commands
| Command | Explanation | Example |
|---|---|---|
id |
Deplays information about the currently logged in user | uid=1000(user01) gid=1000(user01) groups=1000(user01) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 |
id [username] |
Displays information about the specified user | uid=1002(user02) gid=1001(user02) groups=1001(user02) context=unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 |
ps -au |
Lists the processes currently running in a terminal (-a) and lists the user associated with the process (-u) |
 |
¶ passwd
¶ The File
The /etc/passwd file contains information about all the users on the system. It is a seven column file, colon separated. A truncated example is shown below:
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
rhel:x:1000:1000:rhel:/home/rhel:/bin/bash
The columns can be explained as follows:
rhel |
x |
1000 |
1000 |
rhel |
/home/rhel |
/bin/bash |
|---|---|---|---|---|---|---|
| Username | The user's encrypted password used to be stored here. It is now stored in /etc/shadow. See here for info |
UID for this account | GID for this user's primary group | Real name for this user | User's home directory. Where the user will start when they open a shell. User's own configuration data is held here | Default shell program for the user which runs when the user logs in. A system user will use /sbin/nologin as no interactive logins are permitted for system users |
¶ The command
The passwd is used to set the initial password for a new user or to change the password of an existing user.
The 'root' user can set the password to any value, though a message will be displayed if the password does not meet the minimum recommended complexity, but is followed by another prompt to retype the password again and if they match, the password tokens are updated successfully.
A regular user must choose a password which is at least either characters long, not based on a dictionary word, the user name or the previous password.
¶ Shadow
Before the /etc/shadow file, passwords were stored in the /etc/passwd file. The passwd file, however, was readable by all users on the system and would mean that the hashed passwords could be harvested and cracked. As with the passwd, the shadow file has a line per user. The shadow file also allows for password aging and expiration.
A sample file might look like this:
rhel:$6$HdS<SNIP>dK4ZBL/:17933:0:99999:7:2:18113:
And to explain this:
rhel |
$6HdS<SNIP>dK4ZBL/ |
17933 |
0 |
99999 |
7 |
2 |
18113 |
|
|---|---|---|---|---|---|---|---|---|
| Username | encrypted password | Day on which the password was last changed | Minimum number of days which need to elapse before the user can change the password | The maximum number of days a password can be used, it must be changed after this maximum is hit | Warning period. During this time before the maximum the user will be warned about their password expiry | Once the password has expired, it will be accepted for this period. After this has expired, the account will be locked | The day on which the account expires. This is set in days since 1970-01-01 and is calculated in UTC. | The last field is reserved for future use |
¶ Format of encrypted password
$ 6$
HdSxcVs5B5f6ptVH$
eor/EpgPinaDGwBKwgLpqXQlG\<SNIP>
-
Hashing alogorithm used. In this example the '6' indiates that SHA-512 is used (default in RHEL). 1 would indicate MD5 and a 5 would indicate SHA-256.
-
This is the salt used to encrypt the password. Chosen at random
-
The encrypted has of the user's password. The salt and the unencrypted password are combind and encrypted to generate the encrypted hash of the password.
¶ Password aging
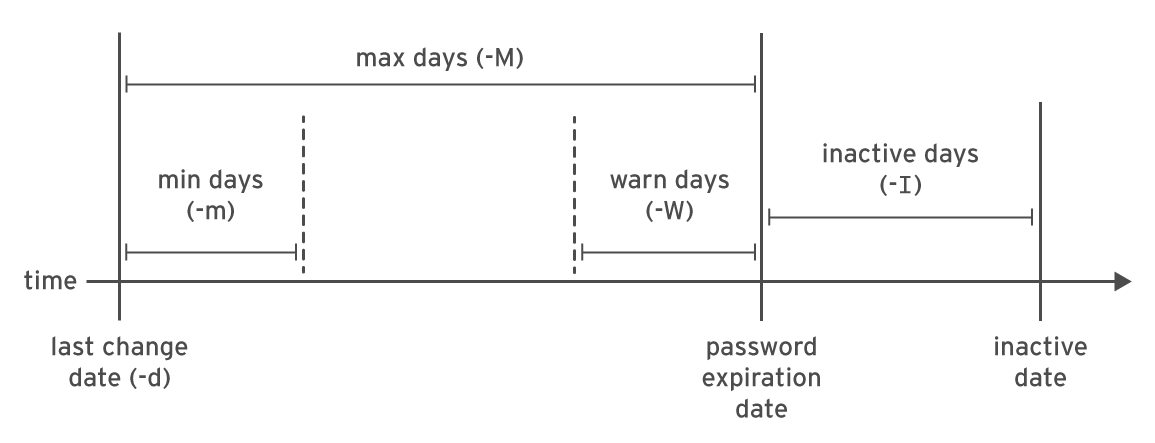
The following diagram show the relevant password aging parameters and how they relate to eacch other. These parameters can be changed using the chage command.
¶ chage options
| Option | Explanation |
|---|---|
-d |
Set date of last password change |
-m |
Minimum age |
-M |
Maximum age |
-W |
Warning period |
-I |
Inactivity period |
¶ Example 1
[user01@host ~]$ chage -d 0 user03`
This will force 'user03' to change their password upon next login
¶ Example 2
[user01@host ~]$ chage -l user03
Displays the password aging details of user03
¶ Example 3
[user01@host ~]$ chage -E 2024-06-09 user03
This will make the user03 account expire on the 9th of June 2024 (given in YYYY-MM-DD format)
The
datecommand can be combined with thechagecommand to calculate dates in the future.date -d "+73 days" -u Sun 11 Feb 16:29:32 UTC 2024
¶ group
Similar to the /etc/passwd, the /etc/group file describes information about groups on the Linux system. As with the passwd file, it is a colon separated file. A truncated example is show below:
root:x:0:root
nobody:x:65534:
adm:x:999:daemon
wheel:x:998:rhel
utmp:x:997:
audio:x:996:
disk:x:995:
input:x:994:
kmem:x:993:
kvm:x:992:libvirt-qemu,qemu
lp:x:991:cups,rhel
The columns can be explained as follows:
kvm |
x |
992 |
libvert-qemu,qemu |
|---|---|---|---|
| Group name | Obsolete group password field. Should always be 'x' | The group's GID | A list of users in the group |
Users will have a primary group and can be members of secondary groups. The primary group is almost always named the same as the user and is created when the user is created. This group will own all of that users created files.
The user's primary group is also known as "User Private Group"
When a user is in a secondary group they are granted access to files based on that group's permissions.
¶ sudo
In some distributions, especially RedHat based distributions, a user who is a member of the 'wheel' group can use sudo to run commands as any user, including 'root'. User will be prompted for their own password.
| Command | Use |
|---|---|
sudo [command] |
Run [command] as superuser |
sudo -i |
Get interactive shell as root user. Useful when needing to log in as root and root has no password set (su - would fail in this instance). |
¶ Configuring sudo
Configuration for the sudo command is done in the /etc/sudoers file. This should be edited with the visudo command.
The line:
%wheel ALL=(ALL) ALL
grants all users in the group wheel access to sudo. To explain a little further:
%wheel |
ALL=(ALL) |
ALL |
|---|---|---|
| Specifies the user or group. In this case, as the line starts with '%' it is a group | This specifies that the group 'wheel' can run any command | The last 'ALL' means that 'wheel' can run those commands as any user on the system |
This can be configured for different users and groups. Here are a few examples:
¶ Example 1
freya ALL=(ALL) ALL
Would mean that the user 'freya' can run all commands ('ALL=(ALL)') as any ('ALL') user on the host.
¶ Example 2
%valhalla ALL=(ALL) ALL
Grants the group 'valhalla' permission to run all commands as any user on the host.
¶ Example 3
odin ALL=(ALL) NOPASSWD:ALL
Grans the user 'odin' permission to run all commands as any user on the host, without having to enter their password (as denoted by 'NOPASSWD:ALL').
This is a security risk and the user account should be carefully protected if doing this
¶ User Adding Modifying Deleting
| Command | Basic Function |
|---|---|
useradd |
Adds user to the system |
usermod |
Modifies a user on the system |
userdel |
Deletes a user from the system |
¶ useradd and usermod
The useradd [username] command adds a user, sets up the home directory for that user as well as creates a private group with the same name as the added user. Important to note that there is no password set at this time and therefore the user cannot log in.
The same options for useradd can be used with usermod to modify user details
The defaults for adding users is loaded from /etc/login.defs.
Some useful options from usermod --help:
| option | Usage |
|---|---|
-c, --comment COMMENT |
Add the user's real name to the comment field |
-g, --gid GROUP |
Specify the primary group for the user account |
-G, --groups GROUPS |
Specify a comma-separated list of supplementary groups for the user account |
-a, --append |
User with the -G option to add the supplementary groups to the user's current set of group memberships instead of replacing them |
-d, --home HOME_DIR |
Specify a particular home directory for the user account |
-m, --move-home |
Move the user's home directory to a new location, must be used in conjunction with the -d option |
-s, --shell SHELL |
Specify a particular login shell for the account |
-L, --lock |
Lock the user account |
-U, --unlock |
Unlock the user account |
¶ Changing user group
| Command | Explanation |
|---|---|
usermod -g fromage brie |
Changes the primary group to "fromage" for the user "brie" |
usermod -aG cheese brie |
Adds the user "brie" to a supplementary/secondary group called "cheese" |
¶ userdel
The userdel [username] command will delete the entry for the given username from the /etc/passwd file, but will leave the home directory intact. In order to delete the user and the user's home directory you must specify the -r option, e.g. userdel -r jotunn.
Deleting a user and leaving the user's home directory intact can lead to security issues. If the user is deleted and the home directory is not removed at the same time, the files are left with the same UID. It is possible when adding a new user again that the old UID is reused, giving the new user access to the old user's files
¶ Group adding modifying deleting
Similar to users, groups can be added, modified and deleted. The comands are also cvery similar:
groupadd- As withuseradd, this command uses the defaults as specified in/etc/login.defsgroupmodgroupdel
| Command | Explanation |
|---|---|
groupadd -g 10000 group01 |
The -g option allows us to specify a GID which deviates from the default |
groupadd -r group02 |
The -r option creates a system group from a range of valid GIDs as per the /etc/login.defs file |
groupmod -n group0022 group02 |
The -n option is for specifying a new name for a group. In the example here we are renaming "group02" to "group0022". |
groupmod -g 20000 group0022 |
In this case, -g option, like with the groupadd command allows us to change the GID |
groupdel group0022 |
This will remove "group0022" |
¶ UID
UIDs (for users) and GIDs (for groups) are usually in specific ranges.
¶ RedHat
| UID range | Purpose |
|---|---|
| 0 | root |
| 1-200 | "system users" assigned statically to system processes by RedHat |
| 201-999 | "system users" which do not own files on the file system. Dynamically assigned from the available pool when the software which requires a system user is installed. These are unprivileged to limit their access to only that which they need |
| 1000+ | Available for assignment to regular users |